MUX VLAN (Multiplex VLAN) provides a mechanism to control network resources through VLAN. Through the two-layer traffic isolation mechanism provided by MUX VLAN, the internal employees of the enterprise can communicate with each other, while the mutual visits between external visitors of the enterprise are isolated. In order to achieve two-layer isolation between packets, users can add different ports to different VLANs, but this will waste limited VLAN resources. The port isolation function can be used to isolate ports in the same VLAN.
In the network with high security requirements, the switch can enable the port security function to prevent illegal MAC address devices from accessing the network; When the number of learned MAC addresses reaches the upper limit, no new MAC addresses will be learned, and only devices with MAC addresses will communicate.
1、MUX VLAN:
For enterprises. It is hoped that internal employees of the enterprise can access each other, while external visitors of the enterprise are isolated. This can be achieved by configuring each visitor to use a different VLAN. However, if the enterprise has a large number of foreign visitors, it will not only consume a lot of VLAN IDs, but also increase the difficulty of network maintenance. The two-layer traffic isolation mechanism provided by MUX VLAN can realize the communication between employees within the enterprise, while the mutual visits between external visitors are isolated.
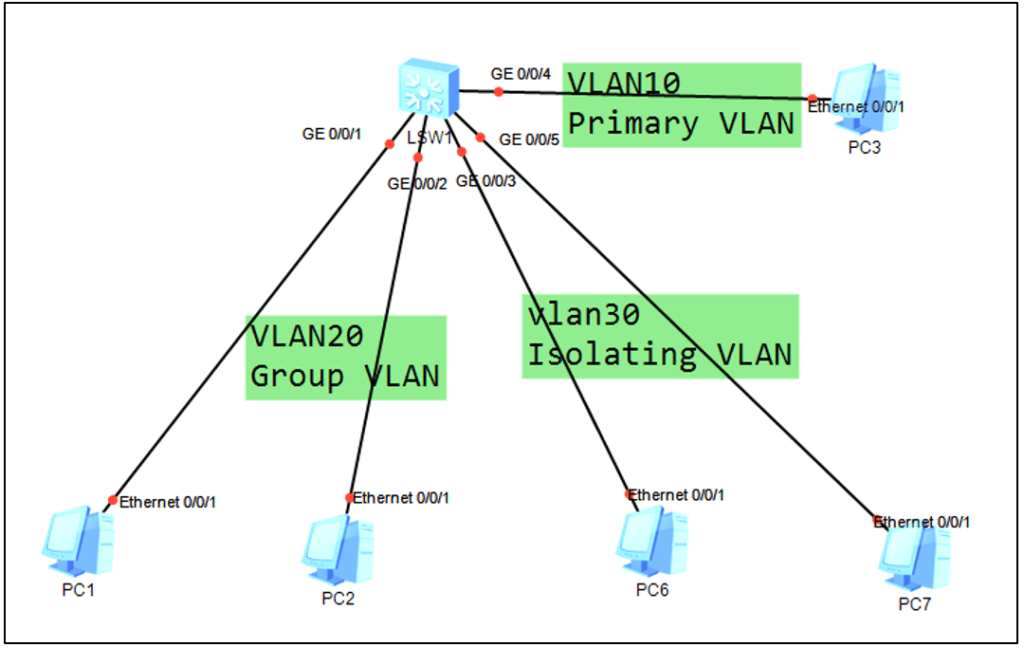
MUX VLAN is divided into master VLAN and slave VLAN, and slave VLAN is divided into isolated slave VLAN and interworking slave VLAN.
Principal VLAN: Principal port can communicate with all interfaces in MUX VLAN.
Separate VLAN: The separate port can only communicate with the principal port, and can be completely isolated from other types of interfaces. Each isolated slave VLAN must be bound with a master VLAN.
Interworking Slave VLAN (Group VLAN): Group port can communicate with Principal port, and interfaces in the same Group can also communicate with each other, but cannot communicate with other Group interfaces or Separate port. Each interworking slave VLAN must be bound with a master VLAN.
2. Port isolation
Port isolation can be divided into two modes: Layer 2 isolation, Layer 3 interworking, and Layer 2 and Layer 3 isolation:
If the user wants to isolate the broadcast message in the same VLAN, but the user under different ports can also carry out Layer 3 communication, the isolation mode can be set to Layer 2 isolation and Layer 3 interworking;
If you want users to be unable to communicate with each other on different ports of the same vlan, you can configure the isolation mode as Layer 2 and Layer 3 isolation.
Port isolation technology also has disadvantages. First, sharing between computers cannot be realized; Second, isolation can only be achieved on one switch, not between stacked switches. If it is a stacked environment, it can only be changed to a cascade connection between switches.
3. Port security
If there are illegal users in the network, you can use port security technology to ensure network security. It is generally used in the following scenarios: ① It is applied to interface layer devices: by configuring port security, it can prevent phishing users from attacking from other ports; ② It is applied to the aggregation layer equipment, and the number of access users can be controlled by configuring port security.
Port Security: In principle, the Port Security feature records the Ethernet MAC address connected to the switch Port through the MAC address table, and only allows a MAC address to communicate through the Port. When packets sent by other MAC addresses pass through this port, the port security feature will prevent it. Port security features can prevent unauthorized devices from accessing the network and enhance security. In addition, the port security feature can also be used to prevent MAC address flooding from filling the MAC address table.